Where’d my Internet go?
Filed Under Geek on 2006-10-06, 23:30
The last week or so my internet connection has been going down seemingly randomly. It’ll go down for awhile and then come back just like normal. What made it odd was that a friend in Texas (I’m in Chicago) was also going down at the same times. After 3 or 4 “coincidences” we decided this wasn’t normal. After narrowing down the similarities, we started looking at our routers, both Linksys WRT54G running the hacked DD-WRT firmware. While it wasn’t a problem with a router, this focused my attention to where I would find the necessary clues.
The next time I lost my connection I noticed the led on my WRT54G router for “Internet” blinking like crazy, indicating a large amount of traffic. I couldn’t even access the router across my lan. I unplugged the router from the cable modem and instantly got access to the web interface. Plugged it back in, no access. Plugged directly into the cable modem with my desktop and got a solid connection again. Whatever is coming through doesn’t affect my Windows machine.
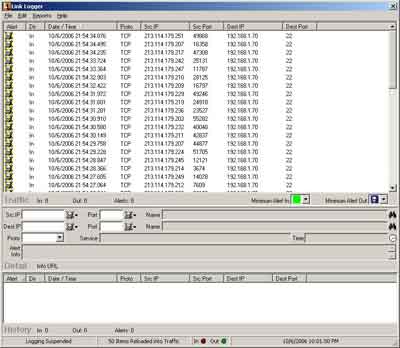
Logging is always good, so I downloaded Link Logger and setup DD-WRT to log to my desktop (see below for how-to) and waited. Sure enough I lost a connection about an hour later. Luckily all the evidence I needed was sitting in Link Logger.
Looks like someone from .se was trying to hammer on my ssh server with multiple machines. Since there are so many machines and so many attempts it was holding me down and not letting anything else through. A typical denial of service. So I unplugged the desktop from the router, plugged directly into the cable modem, power reset the modem to get a new dhcp lease, and started figuring out how to drop the ssh packets. I ssh’ed into DD-WRT while it was not plugged into the internet, and ran the following command line:
iptables -A INPUT --source 213.114.179.0/24 -j DROP
(This will block all incoming traffic from 213.114.179.*)
Of course when I plugged back in, he was no longer hammering, and I didn’t get a chance to test it. I dropped into the DD-WRT web interface, under Administration->Diagnostics and added the iptables command so it will run on startup. This way when I reboot the router it will still have that rule. Let’s hope that stops this mess.
While discussing this with my friend in Texas, we realized the true link between us and these Swedes was not our router, but rather our use of DynDNS. DynDNS is a quick (free) way to get an easy to remember domain that resolves to your home connection. We both have *.homeip.net addresses. I’d be willing to bet these wankers were just scanning for people with homeip.net addresses. Another clue to this was the fact that the attacks were still occurring with IP changes. DD-WRT has an option to automatically update your DynDNS name when your IP changes.
IP Addresses logged: (I wasn’t able to capture all of them as the Trial version of Link Logger doesn’t save them)
213.114.179.203
213.114.179.207
213.114.179.209
213.114.179.210
213.114.179.211
213.114.179.212
213.114.179.214
213.114.179.217
213.114.179.219
213.114.179.224
213.114.179.229
213.114.179.232
213.114.179.236
213.114.179.242
213.114.179.245
213.114.179.247
213.114.179.249
213.114.179.251
All of these resolve to *.cust.bredbandsbolaget.se.
How to log from your router
(This applies to DD-WRT v23 SP1 final)
- Log into the web interface for DD-WRT and go to Administration->Services
- Scroll down and enable “System Log”
- Save Settings
- Scroll back down and provide the IP address of the machine you want to log to.
- Save Settings
- Go to the Administration->Log tab
- Enable the Log, set the Log Level to High, and everything to On (this way everything gets logged)
- Save Settings
- Download and install Link Logger
- Point it to your router’s IP if necessary (Edit menu->Setup->Router Tab)
Tagged: dd-wrt, Linksys WRT54G, stats